Network authentication brute-force tools attempt to loginto a remote
system from a list of provided usernames and passwords. It does so by
sending the credential pairs continuously till the entire provided list
is exhausted. Once, the tool gets a positive response from the remote
system, it stops the attack and displays the username/password pair on
screen which passed the test.It is very unlikely that a hacker would use
network authentication brute-force tools to attack sensitive systems,
because they are very noisy. Every successful or unsuccessful attempt to
log onto the remote system will be logged. Too many login attempts
targeting a single system would surely raise an alarm and the IDS/IPS
would kick-in to thwart the attack.However, only 5 percent of internet
facing servers are monitored by an IDS or IPS.So, there are still ample
of unmonitored systems out there waiting to be exploited by hackers.
In this post, we take a look at Medusa, which is a network authentication brute-forcing tool. It supports a wide array of protocols including FTP, HTTP, SSH, SMB, VNC, POP3, IMAP, MySQL, Telnet and many more. The factor differentiating Medusa is its capability of testing multiple systems in parallel. Medusa achieves this feat through the multithreading directive called ‘pthreads’. Users can specify a list of hosts that are to be tested and Medusa will create a child process for every host and test multiple systems at once leveraging preemptive multitasking to the fullest.
Medusa in action:
1. As can be seen from the screenshot below, the webpage at 192.168.1.1 is asking for credentials through HTTP Basic Authentication.
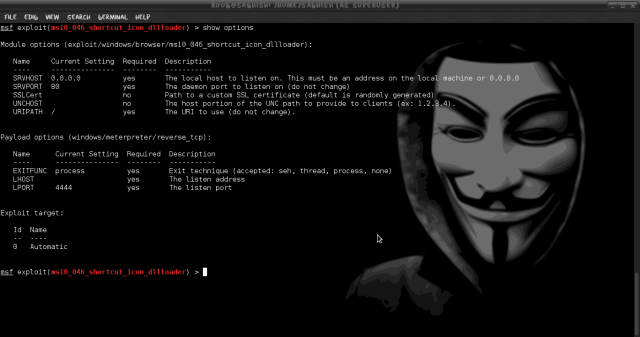
2. To brute-force this authentication, we use the following command:
medusa -h 192.168.1.1 -u admin -P /usr/share/wordlists/rockyou.txt -M HTTP
In this post, we take a look at Medusa, which is a network authentication brute-forcing tool. It supports a wide array of protocols including FTP, HTTP, SSH, SMB, VNC, POP3, IMAP, MySQL, Telnet and many more. The factor differentiating Medusa is its capability of testing multiple systems in parallel. Medusa achieves this feat through the multithreading directive called ‘pthreads’. Users can specify a list of hosts that are to be tested and Medusa will create a child process for every host and test multiple systems at once leveraging preemptive multitasking to the fullest.
Medusa in action:
1. As can be seen from the screenshot below, the webpage at 192.168.1.1 is asking for credentials through HTTP Basic Authentication.
 |
| Authentication Page |
2. To brute-force this authentication, we use the following command:
medusa -h 192.168.1.1 -u admin -P /usr/share/wordlists/rockyou.txt -M HTTP
 |
| Medusa Command |
-h
|
Specifies target. Use -H to provide a list of
targets from a file.
|
-u
|
Specifies username. To keep things simple for this
example we have used the default login ID ‘admin’. Use -U to provide a list
of usernames from a file.
|
-P
|
Specifies Passwords. For this example, we are using
Kali Linux’s default wordlist.
|
-M
|
Specifies Module. Since, we know that we are testing
HTTP Basic authentication, we supply HTTP as the module parameter.
|
3. When Medusa gets a positive response from the remote system, it aborts the test and displays the result on screen as seen below.
 |
| Credentials Found |
Protocols Supported:
AFP
|
Apple Filing Protocol
|
CVS
|
Concurrent Versions System
|
FTP
|
FTP and FTPS (FTP/Auth TLS and FTP over SSL)
|
HTTP
|
HTTP/HTTPS (Basic authentication, NTLM, Digest)
|
IMAP
|
IMAP (143)/IMAPS (993)
|
MS-SQL
|
Medusa auto-detects port number on which the server
is running
|
MySQL
|
Also supports pass-the-hash abilities for pre 4.1
versions.
|
NCP
|
Netware NCP Protocol
|
NNTP
|
Network News Transfer Protocol
|
PcAnywhere
|
|
POP3
|
POP3 (110) and POP3S (995)
|
PostgreSQL
|
Option available to set remote database name
|
REXEC
|
Remote Process Execution
|
RLOGIN
|
Remote Login (513)
|
RSH
|
Remote Shell
|
SMBNT
|
Support all Windows Network Authentication
|
SMTP-AUTH
|
SMTP Authentication with TLS (STARTTLS extension)
|
SMTP-VRFY
|
List of usernames can be provided through -U option
|
SNMP
|
Simple Network Management Protocol
|
SSH
|
Secure Shell
|
SVN
|
Subversion
|
Telnet
|
Telnet (23) and Telnets (992)
|
VMAUTHD
|
VMware Authentication Daemon. Supports both non-SSL
and SSL.
|
VNC
|
Identifies and acts on anti-bruteforcing
functionalities of UltraVNC and RealVNC
|
Web Form
|
Handles GET/POST requests
|
THC Hydra and Ncrack are other network authentication brute-force tools
which are regarded adequately effective. A very good comparison of
Medusa with Hydra and Ncrack can be found HERE
Medusa comes pre-installed in the Kali Linux OS. In case you are using any other Linux distro, Medusa can be downloaded from HERE.
Medusa comes pre-installed in the Kali Linux OS. In case you are using any other Linux distro, Medusa can be downloaded from HERE.